Building Bad: How Architectural Utility is Constrained by Politics and Damaged by Expression
contact | contents | bibliography | illustration credits | ⇦ chapter 6 |
7. SECURITY
Functional requirements for building security address such things as the need to control entry (e.g., in stadiums, museums, homes, etc.; in short, in pretty much all building occupancies) and the prevention of damage from explosive devices. In the first case—to prevent or control entry—physical, electronic, and human means can be deployed (walls, gates, locks; motion sensors, alarms, video cameras; and guards, gatekeepers, bouncers). So much is self-evident and need not be belabored.
What is more interesting is the way in which both physical and psychological ("sociophysical") elements interact to create both the reality and the appearance of security. Creating a real barrier that is designed to prevent unauthorized access to a building (or to a city) is a never-ending contest between the technology of control and the technology of transgression. On the one hand, barrier design is intended to forestall access by unauthorized agents—mainly human—who might attempt to overcome or overwhelm the barrier's physical form by going over, under, or around it, or by penetrating through it. Medieval cities were therefore surrounded by thick and high walls; castles were surrounded by moats; and so on. Surfaces were constructed of materials that were hard enough, high enough, and continuous enough to repulse conventional would-be invaders. As a further disincentive to those who might challenge the integrity of such barriers, weapons could be deployed against invaders from the relatively protected and strategically advantageous sites created for that purpose within or behind the various barriers.
On the other hand, potential invaders might still succeed in breaching defensive barriers by being deceptive (Trojan Horse), technologically more sophisticated (battering ram, catapults, siege towers), or by using any number of alternate strategies that have evolved over time.
In contemporary society, the functional basis of building security presupposes not only the ownership of real property (enforced by state power) that divides a society's geographic surface area into individual parcels from which the owner may lawfully exclude everyone else; but also a pervasive antagonism among the various individuals and classes within that society that makes literal barriers to entry (reinforced by the threat of injury, death, or incarceration faced by would-be intruders) necessary.
As the technology of surveillance becomes more sophisticated and ubiquitous, the requirement for physical barriers that prevent access on the basis of strength, size, and continuity decreases, but is hardly eliminated. Closed-circuit television (CCTV) and other forms of electronic surveillance—including motion- or heat-sensing devices—can trigger alarms or provide identifying information; these act both as disincentive and, for those who nevertheless break through security barriers, as a means of identification and apprehension. The use and potential of surveillance as a deterrent to transgression, admittedly reaching new heights in the 21st century, was nevertheless understood long before the ubiquitous presence of cameras and other electronic devices. Thus, even in the 18th century, "the old simple schema of confinement and enclosure—thick walls, a heavy gate that prevents entering or leaving—began to be replaced by the calculation of openings, of filled and empty spaces, passages and transparencies."1 The classic architectural manifestation of this notion is the so-called Panopticon developed by Jeremy Bentham (1748–1832) in which an observer, the agent of control, could surveille the building's inmates who were arranged in wings radiating from a central tower in which the control agent was situated (Fig. 7.1). That these inmates—whether hospital patients, school children, or prisoners—would not know if they were being watched at any given time was the key insight. It was the mere potential of being watched that sufficed to keep them well behaved.
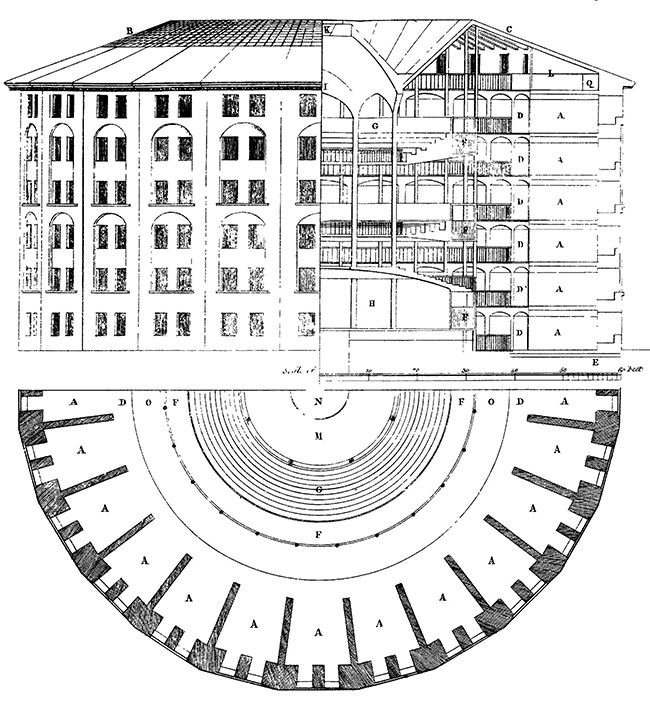
Figure 7.1. Willey Reveley's 1791 drawing, commissioned by Jeremy Bentham, illustrating the Panopticon (from The Works of Jeremy Bentham, vol. IV).
Yet, even modern surveillance devices can be overcome; the contest between control and transgression is hardly over. CCTV cameras can be disconnected or blocked; digital or physical surveillance records can be destroyed; masks can cover faces, increasing the difficulty of identification; gloves can prevent fingerprints (or DNA) from adhering to surfaces; innocent bystanders can be turned into hostages; security personnel, police, and judges can be bribed or otherwise coerced into complicity with criminal acts; and physical force—including bullets and bombs—can be used to confront and contest any power deployed in defense of property.
More importantly, modern interconnected digital networks can be breached, not merely to penetrate a physical space, but to disrupt architectural functions controlled through these networks, or to access data contained on the networks. The infamous theft of 40 million credit and debit card accounts at the American retail giant, Target, is an example of data systems being breached, not to enter buildings or disrupt their functionality, but for their own sake.2 On the other hand, disruption of building functionality can also be the desired outcome. For example, "residents of two apartment buildings in Lappeenranta, a city of around 60,000 people in eastern Finland, were literally left in the cold [when] environmental control systems in their buildings stopped working [because of] a DDoS attack that took them down"3 in 2016, where DDoS stands for "distributed denial-of-service," that is, the deliberate assault on a computer network with so many unwanted messages that normal operation of the system becomes impossible. In fact, environmental control (HVAC) systems are increasingly coordinated through building automation systems, such as BACnet ("Building Automation and Control Networks") in the U.S., a protocol first published by ANSI/ASHRAE in 1995. Such systems are often implemented through the internet so that heating, ventilation, and cooling devices can be controlled or monitored from remote locations. A paper published in 2014 discussing the threats to such systems concluded that "even if security features are available in standards they are commonly not integrated in devices or used in practice."4 Aside from the confusion resulting from multiple protocols, the major issue to overcome, according to Justin Clacherty, is a lack of expertise: "When these systems are installed, the people involved in the deployment are typically electricians whose expertise centres on wiring and physical installation. Integration is often done by electricians who have moved on to different roles. However, security is rarely a discipline that these parties have great expertise in."5
In this context, the U.S. General Services Administration (GSA) has developed strategies to prevent security breaches, especially damage from bombs, by identifying zones within and outside any given building. Various mitigating measures can then be applied to the different zones, depending on the risk (Fig. 7.2). For federal buildings, as an example, the "risk assessment [is] based upon the actual or perceived threat to the building (the events that must be defended against), the vulnerability of that building (the susceptibility to the threat), the consequences if an event should occur, and the probability of that event based upon a variety of factors."6
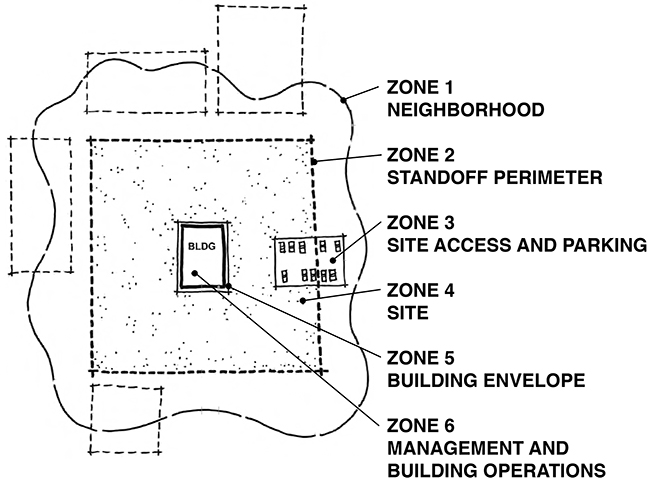
Figure 7.2. The U.S. General Services Administration (GSA) identifies six site security zones in and around buildings: (1) Neighborhood, (2) Standoff perimeter, (3) Site access and parking, (4) Site, (5) Building envelope, and (6) Management and building operations.
In the case of the building enclosure ("Zone 5"), the following possible actions are listed by the GSA: prevent access to vents/air intakes, design emergency egress to allow easy evacuation from a facility, place cameras and light fixtures to maximize visibility, harden the building structure and envelope, and design orientation and massing of building to lessen impact of explosion.7
All of these functional requirements for security are portrayed as a rational response to what is typically mischaracterized as human nature, but in reality derive from the economic compulsion to compete on the basis of one's property. The GSA, in formulating its security guidelines for buildings, puts an almost comical spin on how the unpleasant consequences of capitalism can be turned into something useful for its citizens:
The U.S. General Services Administration (GSA) sees the evolving need for security as an opportunity—to achieve the best design, contribute to the sustainability of the environment, create a portfolio of buildings that will endure into the future, provide safe and productive federal workplaces, and improve the communities in which we work.
In meeting these responsibilities, we demonstrate how thoughtful security design can represent permanence and encourage citizen participation. Increased setbacks can become active public spaces, physical restraints can serve as seating areas or landscape features, and new amenities can both increase the safety of federal employees and integrate our public buildings into their neighborhoods.8
There are also "sociophysical" aspects of building security that have been identified by proponents of defensible space to enable natural surveillance by residents, and to establish both legal and psychological territorial zones.9 Such empirically derived wisdom about safety has two primary flaws. The first flaw is actually inherent in all empirically derived social science. By looking only at what exists, not only are the reasons for such patterns of behavior ignored, but—more fundamentally, and abstracting from such reasons—these prevailing conditions are often considered to be inevitable and unchangeable: a function of human nature. Yet even the empirical basis for such claims—that territoriality explains the form of traditional or primitive settlements—has been challenged. Bill Hillier, in his critique of Oscar Newman's influential book on Defensible Space, argues that this explanation, more often than not, "has failed miserably." He quotes the archaeologist Ruth Tringham, who "concluded that the territoriality/aggression argument 'would seem to have no support in either archaeological or ethnographic evidence: it is rather the simplistic ethnocentric concept of sophisticated guilt-ridden western investigators.' She added: 'The defense and physical demarcation of territory is by no means universal and is dependent on a large number of interrelated factors.'"10
Second, especially with respect to the "natural surveillance" of streets and yards by residents, there is both a sexist and racist undercurrent to the recommendations. The sexist component is the implicit idea that "eyes on the street" are provided mainly by women who stay at home while men are at work. This was undoubtedly true when Jane Jacobs wrote her landmark book with its famous discussion of sidewalk safety in the 1950s (The Death and Life of Great American Cities was published in 1961) and demonstrates the limitations of empirical observations. Thus, in the New Urbanism influenced town of Seaside, Florida, porches facing the street are rarely used and therefore "the social function for which they were designed (that is, to keep eyes on the street and as a place from which to greet passers-by) has not really been realized."11
The racist component is rarely explicit in such studies; rather, the preferred vocabulary involves "strangers," some of whom pose threats.12 The relationship between abstract notions of "territoriality" and racism can be seen in historic segregation and redlining practices that created and preserved ethnically pure neighborhoods. "Redlining," writes Emily Badger, is not just "a practice that exists only in history and our re-tellings of it. … Neighborhoods were ranked and color-coded, and the D-rated ones—shunned for their 'inharmonious' racial groups—were typically outlined in red. … But black communities have warned that it still exists in subtler and changed forms, in bank tactics that have targeted these same neighborhoods for predatory lending, or in new patterns like 'retail redlining.' Some of the persistent redlining, though, still looks an awful lot like the original."13
This relationship can also be seen in the unspoken terror that enforces a de facto segregation in many American neighborhoods. Ta-Nehisi Coates, in Between the World and Me, writes to his son about their prior visits, first to Harlem, and then to Jane Jacobs's idyllic West Village in New York City:
They [white folks] were utterly fearless. I did not understand it until I looked out on the street. That was where I saw white parents pushing double-wide strollers down gentrifying Harlem boulevards in T-shirts and jogging shorts. Or I saw them in conversation with each other, mother and father, while their sons commanded entire sidewalks with their tricycles. The galaxy belonged to them, and as terror was communicated to our children, I saw mastery communicated to theirs. And so when I remember pushing you in your stroller to other parts of the city, the West Village for instance, almost instinctively believing that you should see more, I remember feeling ill at ease, like I had borrowed someone else's heirloom, like I was traveling under an assumed name.14
And this relationship can be seen in the application of "neighborhood watch" strategies within certain neighborhoods; the case of Trayvon Martin is only one of many such instances: "On the night of February 26, 2012, in Sanford, Florida, United States, George Zimmerman fatally shot Trayvon Martin, a 17-year-old African American high school student. Zimmerman, a 28-year-old mixed-race Hispanic man, was the neighborhood watch coordinator for the gated community where Martin was temporarily living and where the shooting took place."15 The ideological justification of cultural separation and "community" comes up again in Chapter 8; and the ideal of community along with the exclusionary concept of a "people" is discussed again in Chapter 14.
Notes
1 Foucault, Discipline and Punish, 172.
2 Brian Krebs, "Target Hackers Broke in Via HVAC Company," Krebs on Security, February 14, 2014, here.
3 Lee Mathews, "Hackers Use DDoS Attack to Cut Heat to Apartments," Forbes, November 7, 2016, here.
4 Szlósarczyk et al., "Towards Suppressing Attacks," 407.
5 Anthony Caruana, "Building Management Systems—Be Afraid, Be Very Afraid," CSO Online, May 26, 2016, accessed November 19, 2019, here.
6 GSA, The Site Security Design Guide, 76.
7 GSA, The Site Security Design Guide, 25.
8 GSA, The Site Security Design Guide, 5.
9 See, for example, Jacobs, The Death and Life of Great American Cities, and Newman, Defensible Space.
10 Hillier, "In Defense of Space," 541.
11 Lang and Moleski, Functionalism Revisited, 117.
12 Jacobs, The Death and Life, 32. "Yet Los Angeles cannot, any more than any other great city, evade the truth that, being a city, it is composed of strangers not all of whom are nice."
13 Emily Badger, "Redlining: Still a Thing," Washington Post, May 28, 2015, here.
14 Coates, Between the World and Me, 89–90 (my italics).
15 Wikipedia, s.v. "Shooting of Trayvon Martin," last modified November 18, 2019, here.
contact | contents | bibliography | illustration credits | ⇦ chapter 6 |

